Cloud security responsibility
Cloud adoption is increasing year after year at a very fast rate. Understandably so when you consider all the benefits cloud adoption offers to operations such as; a low-cost upfront investment in infrastructure, the ability to scale quickly, reduction in time to market, and efficiency. For these reasons the cloud adoption rate has steadily increased over the course of the last few years, and according to Forbes is expected to have over a 80% enterprise adoption rate by 2020. Along with this adoption rate has come confusion and misunderstandings about not only how to securely deploy a cloud their cloud environment but also who is responsible for protecting the data. In this blog post we will discuss where this responsibility lies between the CSP and the customer. Before we dive into who holds what responsibility we must first have an understanding around the different cloud models and what they are. Software as a Service (SaaS), Infrastructure as a Service(IaaS), Platform as a Service(PaaS). Each having a different level of responsibility that the cloud service provider maintains separately from the cloud customer.
Infrastructure as a Service (IaaS), provides infrastructure for the customer to operate on, this alleviating common data center requirements such as the need to purchase hardware or worry about electricity and cooling. The IaaS cloud model being the closest and most familiar to what is usually performed in on-prem allow the customer to keep the most control over their infrastructure as well as maintain the most responsibility over the Operating System, storage, and deployed applications and some control over networking components.
Platform as a Service (PaaS), provides the needed underlying services such as the infrastructure and Operations Systems for the customer to run their application. With this model the customer began to lose control over the infrastructure, network, servers, Operating Systems, and Storage but maintains the control over the configuration settings of the hosted application and in some cases can maintain some configuration control of the hosting environment.
Software as a Service(SaaS), provides less amount of control to the cloud customer. in a SaaS environment, the customer is usually left with minimum user-specific application configuration settings.
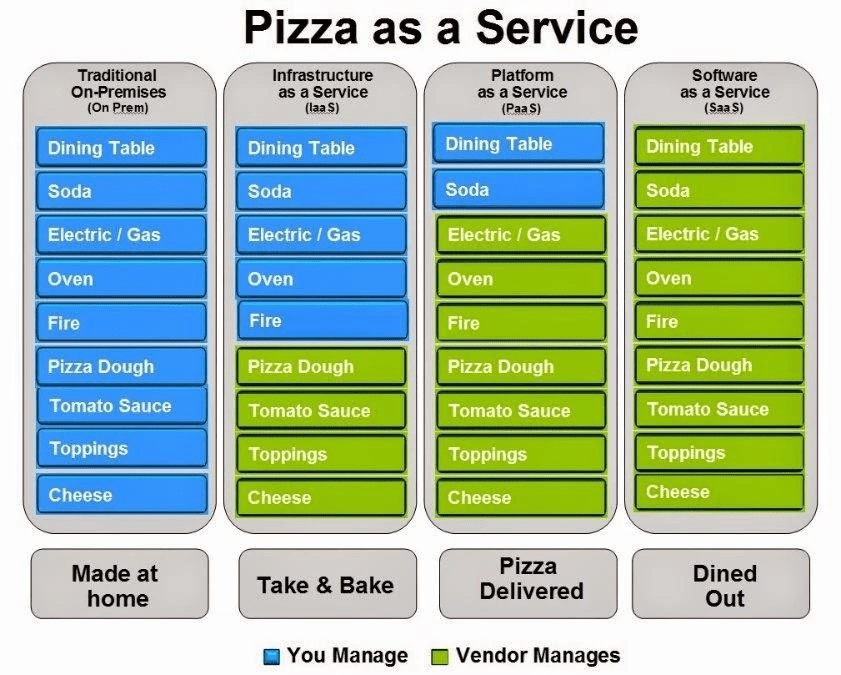
Why is this model important?
As a cybersecurity professional we are in the business of managing risk, the risk of losing data, being hacked, insider threat and various other risks that directly affect information systems in our network. To help us with managing these risks we commonly turn to the Cybersecurity Framework to help guide us on enhancing our cybersecurity posture and improve their ability to prevent, detect, and respond to cyber-attacks. In traditional on-premises infrastructures all security controls undoubtedly stay in control and implemented by the owner. When implementing a cloud model some of those responsibilities shift over to the Cloud Provider that will then have the responsibility around the security control.
An example of security control inheritance in a cloud adoption is Physical and Environmental Protection(PE) family of controls from the NIST 800-53r4. This control requires that the system owner Develop, document, and disseminate policy around the physical access of information systems. Knowing that IaaS models alleviates the need for the cloud customer to maintain physical servers on site, we now know that the Responsibility for these controls will mostly be the responsibility of the cloud service provider and not the owner.
Similar to inherited controls there are also the controls that shared amongst the Cloud Service Provider and the Customer. In most cases these are controls that apply to both infrastructure as well as the customer controlled level. A perfect example of this would be Patch Management, often enough there are patches that get released that may need to be applied to either the infrastructure or to the operating system and application. Although the Cloud Service Provider takes the responsibility over some controls that the system owner inherited this does not in no manner get the CISOCIO or system owners off clear and free. While the responsibility can be transferred to the Cloud Service Provider the system owner and their agents are still held accountable to ensure that all controls are properly being met by their Cloud Service Provider. Accountability of any Security controls can not and should not be transferred.
At End-to-End Computing We offer the best IT security & risk management services in the industry reducing the cost of investing in licensing, new technology, staff and training when adopting cloud technologies. We have over 50+ years of experience offering IT solutions to clients in both the private and public sector. With a team of professionals who can develop and implement services that exceed the expectations of our clients.
Contact us now to get your business or organization secured and request information on our FREE cybersecurity assessment & trial.





